Executive Brief
Don’t use passwords, they’re trivial to crack. Instead, think of your credentials as passphrases, and use “krazy” ones; this, in conjunction with a password manager like Lastpass, will keep your online identity & data much more secure from attack.
Ding dong … the password is dead.
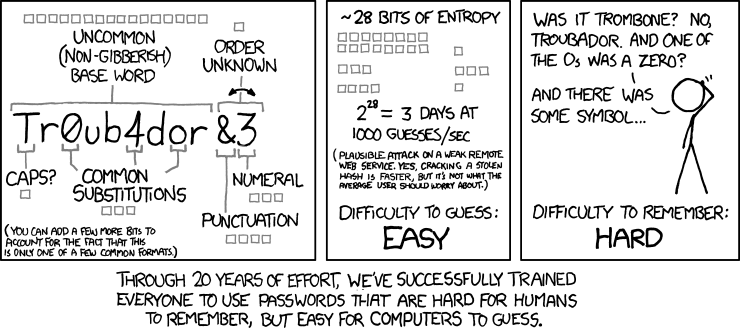
Oh, you’d not heard? It’s true, I’m afraid – passwords are trivially easy to crack, even the seemingly secure, muddled ones, like @n0nyWou5! This variation of the word “anonymous” looks pretty muddled, and hence secure, right? I’ve replaced some letters for symbols and number, and I got all tricksy and flipped the “m” for a “w,” and that ! at the end should really throw off hackers!
Let’s say there’s 500,000 English words in a hacker’s dictionary; cracking a typical password would take a trivially short amount of time, even if each word had to be checked against obfuscations and substitutions, as are present in “@n0nyWou5!”.
So what’s to be done? We should probably sign off the internet and hie ourselves off to the woods, to live off the grid, at one with nature, right? Well, here’s an option to consider before that extreme.
What makes a strong credential? Length + Obscurity
What if we forego the password, and think of your credential in terms of a pass-phrase, instead. By using a phrase – several words strung together – not only is the length of the password increased, but we offset the threat of a dictionary-based based attack. Suddenly, instead of being 1 in 500,000 options, your credential becomes 1 out of billions of possibilities … there are, after all, many, many more ways to strings words together than letters.
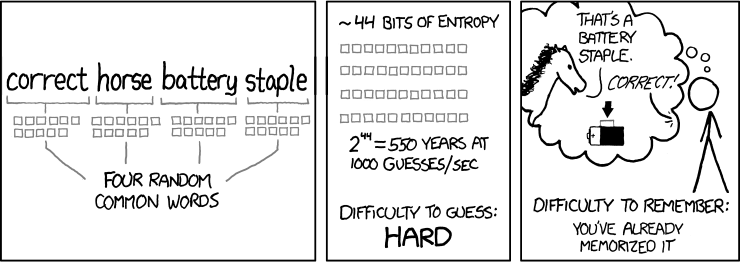
So a pass-phrase, or combination of 4-6 words, automatically gets us the LENGTH we need for a strong credential. For instance, consider the phrase BlueMoonInMarch. That’s 15 characters – not bad; yet as long as it is, it’s still relatively memorable. So is it a good enough to use as a credential?
- outofthepark
- myfluffykitty
- upacreekwithoutapaddle
…since they’re relatively common phrases, they, too, can be cracked with ease.
A secure credential is one that is easy for you to remember, yet hard for others to guess.
Here’s an example: say when I was a kid, my sister decided to paint pink nail polish on our family dog. That’s a unique event, and memorable. Let’s parlay that experience into the phrase PinkGreatDanesareSad. Suddenly, I’ve got pass-phrase that’s personal & unique; nonsensical to anyone else, yet still memorable to me. Sub out some of the letters to meet the “complexity” requirements of many online services, and we land on something like P1nkGreatDanesareS@d.
So there you have it – don’t think of your online credentials as passwords anymore, instead think passphrase. Your credential will be more hacker-proof, yet remain memorable enough that you’re unlikely to need to stick it to your computer with a post-it note 
Finally, to really bring home the point I recommend this informative and amusing snippet (3mins, take the time!) of John Oliver and Edward Snowden talking about passwords.
I’ll leave you with one final thought – please, don’t be the guy at the end of the interview, “I get it … the problem is, I’m not going to do it; because it seems hard, even though I know it isn’t.”
Additional Resources
- Your pass-phrase should be personal & unique, and not a common phrase (e.g., found in quotes, books, social media, etc)
- e., nonsensical to anyone else, memorable to yourself
- Use at least four (4) different words to create your phrase
- Try to have a length of at least 14+ characters
Let’s be conservative, though, and limit the number of words to 500k; so our pass-phrase will be words strung together from two or more words, from a pool of 500k words.
With two (2) random English language words, the number of pass-phrase possibilities is 500,000^2 = 250,000,000,000, or a pool of 250 billion “passwords.”
With four (4) random English language words, this number increases to 500,000^4 = 62,500,000,000,000,000,000,000 = 6.25 X 1022 possible “passwords.”
How Long to Crack?
Brute force cracking depends on the method used to “hash” (encrypt) the password. In 2012 relatively simple password hashes could be cracked using 350 billion guesses per second using computers optimized for password cracking. With our pass-phrase examples above, the 2-word phrase would still be cracked almost immediately whereas, the 4-word phrase would take 5000+ years (here in 2015).
Read more at Wired’s Kill the Password: Why a String of Characters Can’t Protect Us Anymore.



Fascinating stuff. Thanks so much for this tip. I feel like this whole password thing is getting so daunting these days, but this a really easy and even kind of fun way of approaching it. Question: would help to use words and phrases in a foreign/non-English language since the hackers perhaps won’t use foreign dictionaries on American sites?
Good question – I suspect that the majority of attacks probably use an English language dictionary, however it’s really no more difficult to use multiple language dictionaries in an attack.
Still, it’s definitely worth considering combining words from different languages into your passphrase(s) – once again, the key is LENGTH + OBSCURITY.
Note that this technique doesn’t address the issue with remembering MANY passphrases; you’ve probably heard it exhorted that you shouldn’t use the same password across different accounts, and that is absolutely accurate. Given that, sure, one can remember one or two passphrases designed per the above; but once you have more than a few to remember, it can become a mess.
The best approach to using secure and unique credentials is via a “password manager.” A reliable, secure password manager is a complete game-changer, not least because they make your life simpler by automatically filling in your credentials for the many, many web services you use.
Our favorite is LastPass, a secure web service that allows you to synchronize passwords among all your devices, as well as allowing for the use of unique passwords for different accounts very easily. It’s free for use on computers, and a mere $12/year to add in mobile device support.
Other well regarded password managers you can consider are: 1Password, KeePass & RoboForm.
quick update – the lastpass credential manager is a bit out of favor, these days 1Password seems like a better overall solution
Yet another useful article on this topic
https://en.support.wordpress.com/selecting-a-strong-password/