The humble email attachment … arguably the most useful, yet most harmful, electronic communication development of the late 20th century. Once a novelty, email attachments are now as ubiquitous as … well, email itself!
all it takes is one unwary user to open the attachment, causing the malware to infect the computer and spread to others!
There’s no denying how convenient it is to share files with clients, colleagues & friends; unfortunately that very utility has made email a favorite attack vector of the malware community. Hackers quickly realized they could deliver their malware (malicious software) as an email attachment; all it takes is one unwary user to open the attachment, causing the malware to infect the computer and spread to others!
Yet there’s a simple, low-risk solution to ward against this type of attack: block emails with EXE file attachments.
WTF is an EXE?
Computer files come in many different types. Most have a three letter suffix (aka, “file extension”), designating the type of file it is and which app is used to open the file; e.g., DOC for Word, XLS for Excel, PDF for Adobe Reader, ZIP for file archive, etc. So, double-clicking on a file with a name of Land to Far.doc would open up the document in your word processor.
Files with an EXE extension are different – an EXE file is a programs (aka, “executable”), rather than a document. So double-clicking (or otherwise ‘starting’) an EXE will cause the program it contains to run … in itself, not a bad thing, unless that program happens to be malicious.
For instance, recently we’ve seen the reemergence of a threat called CryptoLocker, malware that is about as nasty as it comes. Once activated this threat will encrypts every file it can find, including those on network drives. Once all files have been encrypted, the software than demands a ransom to allow recovery of the files! (read more)
The takeaway? Your data, your company, is at risk by allowing emailed EXE attachments.
What Can Be Done?
You could train staff to “not open emails with EXE attachments,” but oftentimes the EXE will be hidden or wrapped within a legitimate-sounding file. Too, even the most savvy user can make mistakes, and all it takes is accidentally allowing one malicious program to execute on your network to start an electronic pandemic.
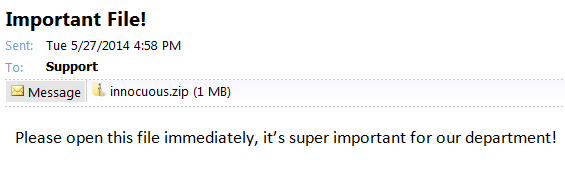
This attachment looks innocuous enough, right?
While the utility of email attachments can’t be denied (nor blocked … your staff may revolt!), the business case for EXE-type file attachments is near nil. So you can significantly reduce the threat of email-based malware – without negatively impacting staff workflow – by blocking emails with EXE-type attachments. The downside risk is very low, as the business case for sending an EXE file through email rarely exists (and if there is a requirement to share an executable, there are safer alternatives, e.g., cloud file sharing).
EXE attachment blocking can typically be accomplished directly at your mail server. Most business-class email systems allow for granular enough control to block EXE attachments, as well as ZIP archives containing EXE files, without affecting legitimate attachments.
Finally, remember that blocking EXE attachments won’t suddenly render all other email attachments safe; it’s not uncommon for malware to “sidejack” non-EXE files (DOC, PDF etc). However, a large amount of malware using email as an attack vector still relies upon EXE attachments, so disallowing EXE attachments should provide protection against a significant number of mail-borne malicious attacks.



Speak Your Mind